It’s no joke. The Revolution Slider WordPress hack has been known for a long time, but companies still are not addressing their website security. It’s national news…read below for a great example of why you need to have security kept up on your website.
Panama Papers: Email Hackable via WordPress, Docs Hackable via Drupal
This entry was posted in WordPress Security on April 11, 2016 by mark (via WF news)
The Mossack Fonseca (MF) data breach, aka Panama Papers, is the largest data breach to journalists in history and includes over 4.8 million emails. Yesterday WF broke the story that MF was running WordPress with a vulnerable version of Revolution Slider and the WordPress server was on the same network as their email servers when the breach occurred.
New information is now released describing how the attackers may have breached the MF email servers via WordPress and Revolution Slider. Below we also summarize below how they probably gained access to client documents via Drupal. We are releasing this information today about the link between WordPress and MF’s email server. The Drupal story has already been covered earlier this week in the media by Forbes (see below), but we are providing some data to support it.
How they hacked email
According to Süddeutsche Zeitung, the German publication that originally received the Panama Papers leak, this is the breakdown of the data structure of the Panama Papers:
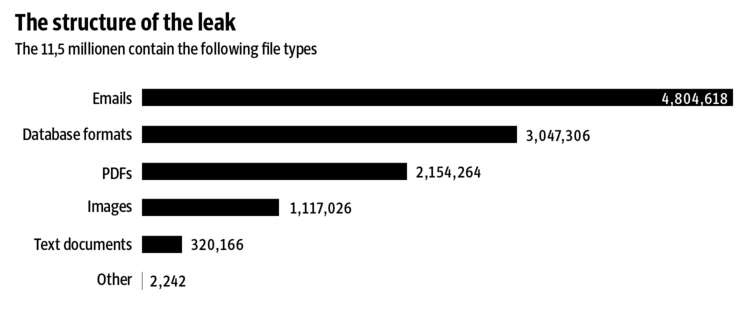
Email is by far the largest chunk of data in the MF breach. Last week MF sent an email to its clients saying that it had experienced unauthorized access of its email servers, confirming that the servers were compromised and making it clear this was in fact a hack.
Yesterday we showed how trivially easy it was to hack into the MF WordPress website via the vulnerable version of Revolution Slider that they were running.
Once you gain access to a WordPress website, you can view the contents of wp-config.php which stores the WordPress database credentials in clear text. The attacker would have used this to access the database.
Our analyst’s research shows that www.mossfon.com is running two plugins in addition to Revolution slider:
MF are running the WP SMTP plugin which gives you the ability to send mail from your website via a mail server. This plugin stores email server address and login information in plain text in the WordPress database. The login information stored is a mail server SMTP login for sending email. Here is a screenshot showing the login information for this plugin appearing in a database as plain text on one of our test servers:
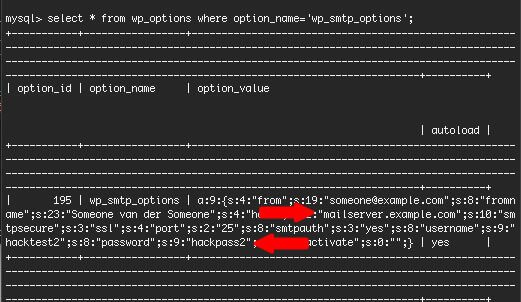
As you can see above, once an attacker had access to WordPress, the wp-config.php file which contains the database credentials and then the WordPress database, they can see the mail server address and a username and password to sign-in and begin to send email. They would also have had whatever other privileges were conferred on that account.
MF are also running the ALO EasyMail Newsletter plugin which provides list management functionality. One of the functions it provides is to receive bounced emails from a mail server and automatically remove those bounced mails from the subscriber list. To do this, the plugin needs access to read emails from the email server. This plugin also stores email server login information in the WordPress database in plain text. In this case the login information provides the ability to receive mail via POP or IMAP from the mail server. The screenshot below shows how this plugin stores email server login information:

Once the attacker also had access to this data, after gaining access to the WordPress database via Revolution Slider, they would have been able to sign-into the email server and would be able to read emails via POP or IMAP.
To summarize the attackers movement
We think it is likely that an attacker gained access to the MF WordPress website via a well known Revolution Slider vulnerability. This vulnerability is trivially easy to exploit as we demonstrated in our research released yesterday.
This would have given them access to the WordPress database. The research we released today shows that MF are running two additional plugins that store login information for their email server in plain text in the database. The attacker would have read this information from the WordPress database and used it to gain access to the email server.
Did they enforce the principle of least privilege?
One of the key concepts in information security is the principle of least privilege. For example: User accounts should only have the access they need to do their job. Did MF configure those WordPress plugin email accounts so that they could only receive bounces and send web based emails?
It’s easy to imagine in a company with high powered clients, the same account that a customer relationship manager uses is also used to send list emails. This would ensure that the manager sees all replies in his or her inbox. If that was the case, the attacker would have gained access to a senior staff member’s email account when they stole these email server credentials.
How attackers probably gained access to client corporate documents
We’re going to briefly summarize how attackers probably gained access to client corporate documents like PDF’s. According to the Mossfon client portal website, “The Mossfon Client Information Portal is a secure online account that enables to access your corporate information anywhere and everywhere, with real time updates of your ongoing request.”.
The MF client portal that provides clients access to data was running (and continues to run) a version of Drupal that has over 23 vulnerabilities. This version was responsible for “Drupageddon“, a mass hacking of Drupal sites. This link to mossfon.com’s drupal changelog shows they are still running an old vulnerable version of Drupal. Here’s a screenshot:

Breaking into this system wouldn’t even tax a beginner security analyst. Once an attacker compromised the client login permissions system which is Drupal powered, they would have defeated any access control and could access any client corporate information. We think this is a likely vector used to steal client PDF’s and other documents. The weakness in MF’s Drupal website was first covered by Fortune earlier this week.
Conclusion
It was demonstrated that Mossack Fonseca had a Revolution Slider vulnerability in their WordPress site which probably gave an attacker initial access to their systems including their WordPress database. Now it is demonstrated how the attacker could move from their WordPress installation into MF’s email systems and begin to compromise email which formed the bulk of the data breach in the Panama Papers.
